Truebit’s TRU token crashes over 99% after a 26 million dollar Ether exploit, extending a string of major DeFi security breaches despite falling aggregate losses.
Summary
- Truebit reports a smart‑contract exploit that drained about 8,535 ETH, or roughly 26 million dollars, triggering a 99% crash in TRU’s price.
- December also saw Flow’s 3.9 million dollar counterfeit token incident and a Trust Wallet Chrome extension hack costing users around 7 million dollars.
- PeckShield data show total crypto hack losses fell to about 76 million dollars in December from 194 million in November, even as high‑profile breaches multiplied.
Truebit acknowledged “an incident of security involving one or more malicious actors” tied to a smart contract address that suggests losses of about 26 million dollars in Ether. In a post on X, the team said it was in contact with law enforcement and was “taking all available measures” following the breach, but has not yet given a detailed technical post‑mortem.
On‑chain analysts monitoring the protocol reported that the attacker siphoned off around 8,535 ETH, valued at roughly 26.6 million dollars at the time. While the contract address flagged by Truebit shows only small amounts of stolen ETH, blockchain sleuths such as Lookonchain and others have pointed to a broader pattern of movements indicating that “the total amount of cryptocurrency stolen in the attack exceeded 26 million dollars.”
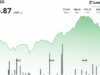
Market reaction was brutal and immediate. According to data from Nansen, the price of Truebit’s TRU token plunged more than 99%, sliding from roughly 0.16 dollars to an all‑time low near 0.0000000029 dollars as reports of the exploit spread. At the time of publication, it remained unclear what exactly triggered the multi‑million‑dollar exploit or whether end‑user funds held on the protocol were directly at risk, and Cointelegraph noted that Truebit had not responded to a request for comment.
Flow’s counterfeit token incident
The Truebit breach follows a December in which multiple high‑profile exploits shook confidence in blockchain infrastructure. On 27 December 2025, the Flow Foundation disclosed that an attacker exploited a vulnerability in the Flow network to “counterfeit tokens, extracting approximately 3.9 million USD.”
In its technical post‑mortem, Flow stressed that “no existing user balances were accessed or compromised” and that the attack duplicated assets rather than touching legitimate holdings. Validators coordinated a network halt within about six hours of the first malicious transaction, and most counterfeit assets were either frozen on‑chain or recovered and destroyed in coordination with exchanges.
Trust Wallet’s malicious Chrome update
Trust Wallet also faced a major security failure in late December when its Chrome browser extension was compromised. The company later confirmed that version 2.68 of the extension contained malicious code that enabled an attacker to access sensitive wallet data and drain user funds, ultimately leading to estimated losses of around 7 million dollars.
Trust Wallet urged users to update immediately to version 2.69 and launched a reimbursement process, warning of secondary scams via fake compensation forms and impersonated support accounts. CEO Eowyn Chen said the malicious build “was most likely published externally through the Chrome Web Store API key, bypassing our standard release checks,” underscoring the supply‑chain dimension of the compromise.
Industry‑wide losses and security trend
Despite the succession of large breaches, industry‑wide losses from hacks and exploits actually fell into year‑end. Blockchain analytics firm PeckShield reported that total losses across the crypto sector dropped to about 76 million dollars in December, down sharply from roughly 194 million in November.